Understanding What Really Happens When Systems Fail
Imagine a line of dominoes. One tiny piece tips over, and suddenly, the whole thing comes crashing down. That's often what IT system failures feel like. A seemingly minor hiccup can quickly snowball into a major disruption, impacting everything from your ability to serve customers to how your own team functions internally.
This isn't just about a website going offline. It's about the chain reaction that follows: lost productivity, damaged relationships with clients, and the potential for significant financial losses.
The Real Cost of Downtime
Think about a busy e-commerce site during a big sale. What happens if a server suddenly malfunctions? Customers can't complete their purchases. This translates directly into lost revenue and frustrated shoppers who may just give up and go somewhere else.
Meanwhile, your team is scrambling to fix the problem, pulling valuable resources away from other important tasks. This reactive, "firefighting" mode is not a sustainable way to operate.
The Growing Threat of IT Incidents
IT incidents are a serious and growing concern. A recent survey found that a staggering 88% of executives expect a major global IT outage in the next year. You can find more details in this report on executive expectations for IT outages.
This highlights the urgent need for a solid IT incident management process. It's not just about fixing problems when they arise; it's about preventing them in the first place.
Moving Beyond Break-Fix
To truly grasp the full picture, take a look at this article on the overall Incident Management Process. A well-designed process goes beyond simply addressing the immediate issue. It's about understanding the root cause of the failure and taking steps to stop it from happening again. This proactive approach is essential for long-term stability and growth.
Want to learn more? Our guide on incident management workflow offers a deeper dive into this critical process. It's about shifting from a reactive break-fix cycle to a proactive, resilient system that can handle the inevitable challenges that come with running a business.
Following the Trail From Problem to Solution
Ever wonder how the best IT teams stay calm amidst digital storms? Their secret? A rock-solid IT incident management process. Think of it as a roadmap guiding them from the first flicker of a problem to its complete resolution. This journey transforms chaos into control, ensuring smooth sailing for everyone.
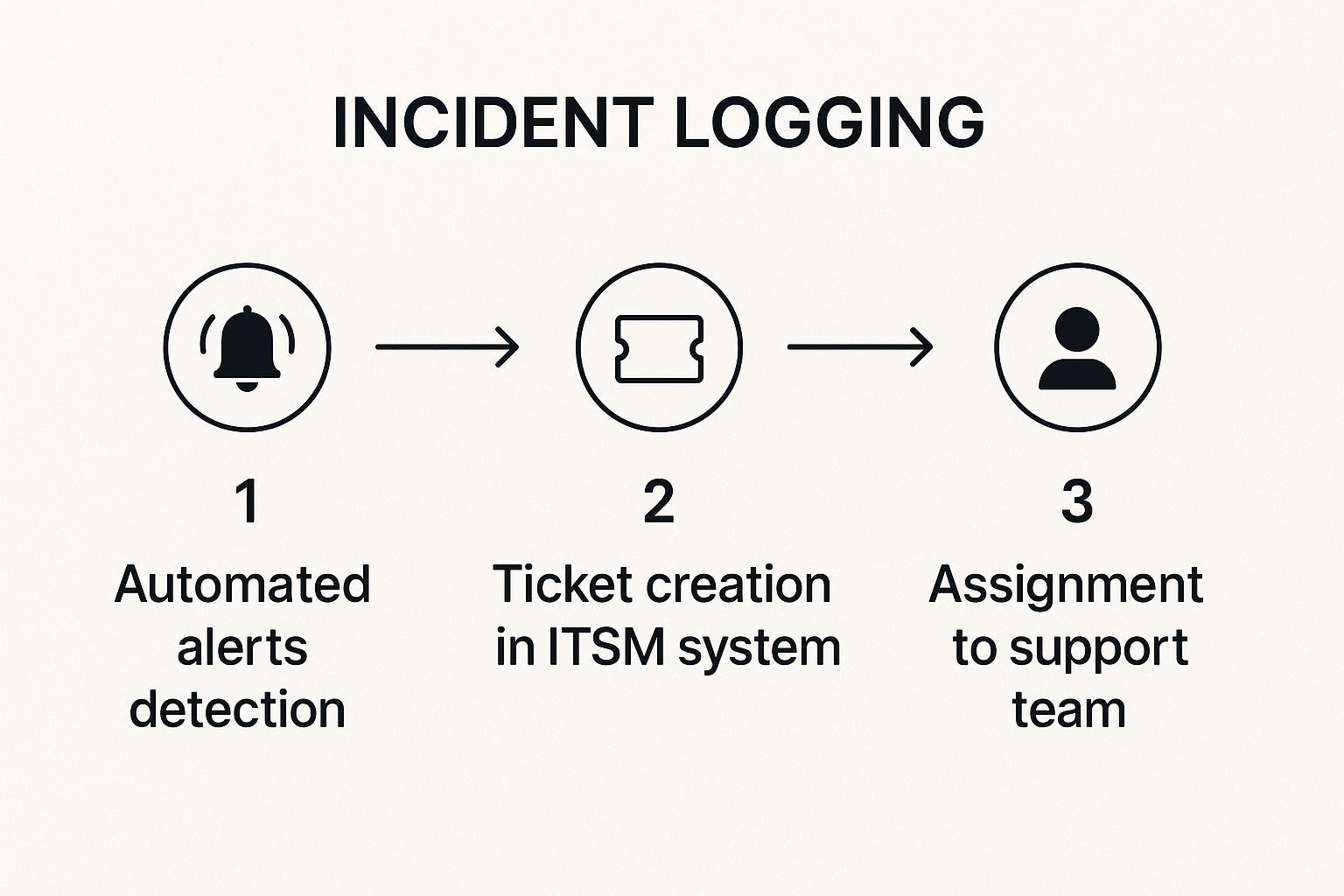
The first step is early detection. Imagine a smoke detector—you want it to go off at the first whiff of smoke, not when the house is ablaze. Automated monitoring systems are like those detectors, often catching issues before users even realize something's amiss.
The infographic above illustrates this initial workflow. An automated alert triggers a new ticket, which is then routed to the right support team. This streamlined process ensures every blip on the radar gets a documented response, preventing incidents from falling through the cracks.
Triaging Incidents: Prioritizing Problems
But not all incidents are created equal. A minor glitch isn't the same as a system-wide outage. That's where triage comes in. Just like in a hospital emergency room, IT teams need to prioritize. This ensures resources are focused on the most critical issues, preventing overreactions and keeping everything running smoothly.
Investigating and Resolving: Finding the Root Cause
Once prioritized, the investigation begins. Like detectives, IT professionals piece together clues to pinpoint the root cause. This might involve digging through logs, talking to users, or running diagnostic tests. The goal is to understand not just what happened, but why it happened.
Resolution strategies then come into play. A quick patch might temporarily fix things, but addressing the underlying problem prevents future headaches. Think of it like treating the illness, not just the symptoms. Interestingly, the average time to detect a breach is a staggering 204 days, with another 54 days needed for containment. That’s over eight months! This highlights just how crucial effective incident management really is. For a deeper look into what executives expect regarding IT outages, check out this resource: executive expectations for IT outages.
Learning From Experience: The Post-Incident Review
The final, and perhaps most crucial, step is the post-incident review. This isn't about pointing fingers; it's a learning opportunity. What went well? What could be improved? How can we prevent this from happening again? This continuous improvement cycle transforms IT teams from reactive firefighters into proactive problem-solvers.
It's also important to distinguish between incident management and crisis management. While related, they're not the same. Incident management deals with individual events, while crisis management addresses larger, more impactful disruptions. For more on IT crisis management, see this helpful resource: IT crisis management.
Let's take a closer look at the typical timeline and key activities involved in each phase of the incident lifecycle:
To better understand the time allocation and key activities involved in managing IT incidents, let's look at the following table:
Incident Lifecycle Phases Comparison
| Phase | Typical Duration | Key Activities | Success Metrics |
|---|---|---|---|
| Detection | Minutes to Hours | Automated alerts, monitoring tools, user reports | Mean Time to Detect (MTTD) |
| Triage | Minutes | Prioritization based on impact and urgency | Time to triage, number of incidents escalated |
| Investigation | Hours to Days | Root cause analysis, log analysis, user interviews | Mean Time to Investigate (MTTI) |
| Resolution | Minutes to Days | Implementing fixes, testing, communication | Mean Time to Resolve (MTTR), customer satisfaction |
| Post-Incident Review | Days to Weeks | Documentation, analysis of incident data, identifying improvements | Number of preventative actions implemented, reduction in similar incidents |
This table summarizes the key activities and success metrics for each phase, giving you a clear overview of the entire incident management lifecycle. By tracking these metrics, teams can continuously improve their response times and minimize the impact of future incidents. Remember, effective incident management is all about learning from the past to build a more resilient future.
Building Your Incident Response Dream Team
What separates a smooth incident response from a chaotic free-for-all? It's the team. Imagine a Formula 1 pit crew: highly trained specialists, each with a specific job, working with incredible speed and precision. That's the kind of coordinated efficiency you need when your systems go down. Building this "dream team" starts with defining crystal-clear roles and responsibilities within your IT incident management process.
The Incident Commander: Leading the Charge
Every successful response needs a leader: the Incident Commander. Think of a conductor leading an orchestra. This person directs the entire response effort, making crucial decisions and keeping everyone on the same page. This role requires strong communication and decision-making skills, arguably even more than in-depth technical expertise.
First Responders: The Front Line
These are your initial point of contact, like the EMTs arriving at an accident scene. They assess the situation, collect initial information, and try to resolve the issue. Their technical chops are essential, but their ability to communicate clearly and calmly under pressure is just as vital.
Subject Matter Experts: Deep Dive Specialists
Sometimes, incidents require specialized knowledge. These experts might not be part of your core IT team, but they possess invaluable business or technical knowledge that can be critical during complex incidents. They're like specialized doctors called in for a difficult surgery.
Role Escalation: Knowing When to Call for Backup
Not every incident can be resolved by the first responder. Having a clear escalation path is vital. This ensures that when initial attempts fail, the incident is smoothly handed off to someone with the appropriate expertise. This avoids the dreaded "too many cooks in the kitchen" scenario, making sure the right people are engaged at the right time. For smooth transitions, consider how incident management integrates with broader IT service management (ITSM). This helps connect incident response to overall IT strategies, especially for those familiar with System Integration Services.
Balancing Expertise and Efficiency
The goal is to have enough expertise on hand without creating chaos. Too many people can lead to confusion and actually slow down the process. Effective teams find the right balance, ensuring quick access to specialized skills while keeping the response streamlined and focused. This efficient structure empowers teams to swiftly diagnose, address, and resolve incidents, minimizing downtime and maximizing organizational productivity within the IT incident management process. By clearly defining roles and responsibilities, organizations lay a solid foundation for effectively handling any IT disruption.
Preventing Fires Instead of Fighting Them
The best way to manage IT incidents isn't about heroically extinguishing flames, but about stopping them from igniting in the first place. Rather than constantly reacting to emergencies, leading IT teams are proactively identifying and addressing potential issues before they become full-blown crises. This represents a significant shift – moving from reactive firefighting to strategic prevention. Let's explore how forward-thinking organizations are transforming their IT incident management process.
The Power of Prediction: Anticipating Problems
Think of traditional incident management like a smoke detector – it only alerts you when the room is already filled with smoke. Modern systems, however, are far more intelligent. Using the power of AI and intelligent automation tools, they can now analyze system behavior and identify subtle warning signs, much like noticing a smoldering ember before it sparks a major fire.
Imagine a server gradually exhibiting slightly higher CPU usage over several days. A traditional system might wait until usage crosses a critical threshold before triggering an alert. An AI-powered system, on the other hand, can detect this creeping increase and recognize it as a potential precursor to a system crash. This allows the team to address the issue proactively, perhaps during a scheduled maintenance window, avoiding a frantic 3 AM call.
Reducing Alert Fatigue: Focusing on What Matters
One of the biggest headaches in incident management is alert fatigue. Being constantly bombarded with notifications eventually desensitizes teams, making them more likely to overlook critical warnings. Proactive systems tackle this issue by filtering out the noise and focusing on actionable insights derived from complex pattern recognition. This ensures that teams receive only the most relevant alerts, allowing them to concentrate on real threats rather than minor fluctuations.
This proactive approach is further reinforced by the growing use of AI and automation tools, allowing organizations to detect and respond to incidents more effectively. For example, some companies using AI-powered security tools have cut their breach detection times significantly – from an average of 204 days down to 102 days. To learn more about these trends, check out these incident response statistics. This shift toward proactive security drastically improves an organization's ability to neutralize threats before they inflict serious damage.
Integrating with Change Management: Preventing Deployment Disasters
Many IT incidents stem from changes or deployments that weren't properly planned. A proactive IT incident management process seamlessly integrates with change management. By assessing the potential impact of changes before implementation, organizations can identify and mitigate risks early. This means fewer unexpected issues and smoother transitions during deployments. This proactive approach helps teams address potential problems before they disrupt operations, ensuring changes are rolled out safely and efficiently, minimizing incident risk, and maximizing system stability.
Mastering Crisis Communication Without Creating Panic
When IT systems go down and stress levels skyrocket, clear communication is often the first casualty. But communicating effectively during an IT incident is absolutely essential. It's like the oxygen mask on an airplane – you have to secure your own oxygen supply before assisting others. This section explores how experienced incident managers stay calm and keep stakeholders informed throughout the IT incident management process, preventing panic and building confidence.
The Psychology of Effective Updates
Generic messages like "we're working on it" are actually counterproductive. They breed anxiety and uncertainty. People crave concrete information, not vague platitudes. Imagine a doctor telling a worried patient, "We're doing something." Not very reassuring, is it? Instead, providing specific updates, even if they're not ideal, builds trust and reduces panic. A message like, "We've pinpointed the problem as a database error and are applying a fix. We anticipate full restoration within the hour" is much more effective.
Providing regular, transparent updates, even when the news isn't great, builds trust and demonstrates that you're in control of the situation.
Tailoring Messages to Your Audience
Different stakeholders require different information. Executives want the strategic overview: How will this impact the business? End-users need practical timelines: When can I get back to work? Crafting messages tailored to each audience ensures everyone receives the information they need, without being bombarded by irrelevant details. A good analogy is a newspaper – different sections cater to different interests. You wouldn't expect the sports section to delve into financial market analysis. Learn more about effective communication strategies in our article about Escalation Process Template.
Establishing Communication Rhythms
A constant barrage of updates can overwhelm your response team and create unnecessary noise. Establishing a regular communication cadence – for example, every 30 minutes for major incidents – provides a predictable flow of information without disrupting the work itself. Think of it like a metronome – providing a steady, consistent beat for the response effort. This regular rhythm reassures stakeholders that progress is being made.
Using Multiple Channels
Modern organizations utilize various communication channels – email, Slack, SMS – to ensure information reaches everyone through their preferred medium. Imagine a critical system outage affecting remote workers. Sending an email might be useless if they can't access their inbox. A text message, however, could be the lifeline they need. A multi-channel approach ensures redundancy and maximizes reach, keeping everyone in the loop during an incident.
To help illustrate how to best communicate with various stakeholders during an incident, take a look at the table below:
Stakeholder Communication Matrix
This table provides a breakdown of communication frequency, channels, and content types for different stakeholder groups during incidents. Understanding these nuances helps tailor your communication for maximum impact.
| Stakeholder Group | Update Frequency | Communication Channel | Information Level |
|---|---|---|---|
| Executive Team | Hourly | Email, Direct Call | High-level impact, business continuity plans |
| IT Team | Every 15-30 minutes | Slack, Internal Chat, PagerDuty | Technical details, resolution progress |
| End-Users | Every 30-60 minutes | Email, Service Portal, SMS | Service disruption details, estimated restoration time |
| Customers | As needed | Website banner, Social Media | General service disruption notice, contact information |
Key takeaways from this matrix include the importance of frequent updates for the IT team directly involved in resolution, and the focus on high-level impact for executives. Customers and end-users primarily need to know the status of the disruption and when they can expect services to resume.
By mastering these communication strategies, incident managers become anchors of stability in turbulent situations. They keep stakeholders informed, manage expectations, and project an air of calm control, even amidst the most challenging IT incidents. This clear and consistent communication cultivates trust, minimizes panic, and ultimately contributes to a more efficient and effective IT incident management process.
Measuring What Actually Matters for Improvement
Let's be honest: many organizations miss the mark when measuring the effectiveness of their IT incident management process. They focus on the wrong things – like a restaurant obsessed with how fast tables are cleared, not how much diners enjoyed their meals. Speed is important, sure, but there's a bigger picture. To truly gauge your incident management performance, you need to look beyond simple averages.
Beyond Mean Time to Recovery (MTTR)
Mean Time to Recovery (MTTR) is often the go-to metric, but it can be misleading. Imagine two teams: Team A resolves incidents quickly with band-aid solutions, while Team B takes a bit longer but fixes the root cause. Team A might have a lower MTTR, but they're probably fighting the same fires over and over. Real success is about preventing repeat incidents, not just putting them out quickly.
Balancing Leading and Lagging Indicators
Think of it like driving. Your speedometer (a lagging indicator) shows how fast you've been going, while the road ahead (a leading indicator) guides your future actions. Likewise, you need both lagging indicators like MTTR to understand past performance and leading indicators to anticipate potential problems. Leading indicators might include things like proactive system upgrades or regular security checks.
The Power of Post-Incident Reviews
The best teams treat post-incident reviews like valuable learning opportunities, not finger-pointing exercises. Think of them as debriefings after a project, a chance to identify weak spots and improve future responses. These reviews are key for continuous improvement and building a more resilient IT incident management process.
Tracking Meaningful Trends
Instead of getting bogged down in isolated incidents, watch for trends over time. Are you seeing fewer major incidents? Is the resolution time for specific incident types improving? These trends paint a much clearer picture of your overall progress. You might also find value in exploring broader performance measurement strategies like those discussed in our guide on customer service metrics.
Demonstrating Business Value
When talking metrics with executives, connect them to business outcomes. Don't just say "we reduced MTTR by 15%". Say "by reducing MTTR, we saved the company an estimated $X in lost productivity and boosted customer satisfaction by Y%." This highlights the true value of your IT incident management process and its impact on the bottom line. By focusing on the right metrics and presenting them effectively, you can shift incident management from a cost center to a strategic asset, strengthening your organization's resilience.
Key Takeaways
Your journey to understanding and implementing a robust IT incident management process doesn't end with fixing the immediate problem. It's about creating a system for continuous improvement and proactive prevention. Think of it like shifting from constantly putting out fires to designing a fireproof building.
The image above shows the ITIL v3 Service Lifecycle, a framework for managing IT services. Incident management is a key part of this lifecycle, like the rapid response team within a larger organization. Its focus is getting things back up and running as quickly as possible. Notice how incident management sits within the bigger picture. This integration with other service management processes is essential. It ensures that the lessons learned from resolving incidents contribute to overall service improvements.
Key Actions for Success
Here’s what you need to make incident management work effectively:
-
Establish Clear Roles: Define who does what during an incident. Think of a surgical team: everyone knows their role and works together seamlessly. The same clarity is needed for incident response.
-
Prioritize Effectively: Not all incidents are created equal. Some are minor inconveniences, others are full-blown emergencies. Focus on the incidents with the biggest impact – the ones that really matter.
-
Communicate Clearly: Keep everyone in the loop, but avoid causing unnecessary panic. Clear and honest communication builds trust with stakeholders. Imagine a pilot calmly explaining turbulence – that’s the kind of communication we’re aiming for.
-
Learn from Every Incident: Post-incident reviews are invaluable. They're like a debrief after a project. Ask yourselves: What went well? What could we improve? These reviews are your roadmap to a better system.
Building Long-Term Resilience
A robust IT incident management process is an investment, not a band-aid. It requires a commitment to continuous improvement and a willingness to learn from every bump in the road. Don’t try to do everything at once. Start small, focus on the most impactful changes, and track your progress. Over time, you’ll build a resilient IT system that can handle anything that comes its way – think of it as building a dam to prevent future floods.
Ready to move your incident management from reactive to proactive? Screendesk gives your team the tools to communicate effectively, resolve incidents efficiently, and prevent future disruptions.